Just when you thought it was safe to go back in the [email] water… Phishing gets serious. Of course, you should never let your guard down on phishing and spoofing, but there’s a bigger shark in the water now; one that impersonates important people within an organization. This new type of scam is referred to as Business Email Compromise, or “BEC.” These emails use similar tactics to phishing but are much more targeted, and directed at a specific individual or a small group or individuals. They prey on the fact most people will not question a company executive or a vendor making changes to their systems.
Let’s put ourselves in the shoes of a scammer. Where do you want to spend your time when you’re working? You’ll likely say, “On things that will produce the best value for the effort. Phishing a consumer might net a few hundred to a couple thousand dollars at a time. Why not look at a different target with much deeper pockets? In 2019, the FBI released a report stating “In 2019, the IC3 received 23,775 Business Email Compromise (BEC) / Email Account Compromise (EAC) complaints with adjusted losses of over $1.7 billion.”
There are several variations of BEC fraud to consider, but they all operate with similar tactics and targets:
- Someone poses as a company’s executive and instructs staff to make a wire transfer into the fraudulent account.
- Fraudster poses as an IT services department at a financial institution saying they want to make a test transfer, resulting in an actual transfer.
- Fraudsters claim to be a corporate supplier and ask for outstanding invoices to be paid into a different bank account than usual.
- Employees click on links within phishing emails containing malware, providing credentials to make transfers on their own.
How do BEC scams work?
Typically, an individual within a finance role will be the targeted victim. Why? They likely have access to conduct money transfers for an organization. The scam usually starts with a generic email trying to get a response from the intended target. It could be something as simple as, “Are you in the office today?” While responding, the individual is providing all kinds of useful details about themselves and their organizational role. How? An email signature, which is commonly included in corporate emails and contains information such as phone number, proper title, and full name.
The second contact often comes with a request about an upcoming purchase or a potential bill needing to be paid quickly, in secret, or with little information from the requestor. The next contact could outline a secret deal to buy a company, or the purchase of goods and services from a new vendor. These will also usually arrive from an email address similar in nature to the actual individual being impersonated, but not from their actual email address (i.e., from a Yahoo or Gmail account instead). This is used to circumvent authentication solutions such as SPF, DKIM, and DMARC used on a business domain.
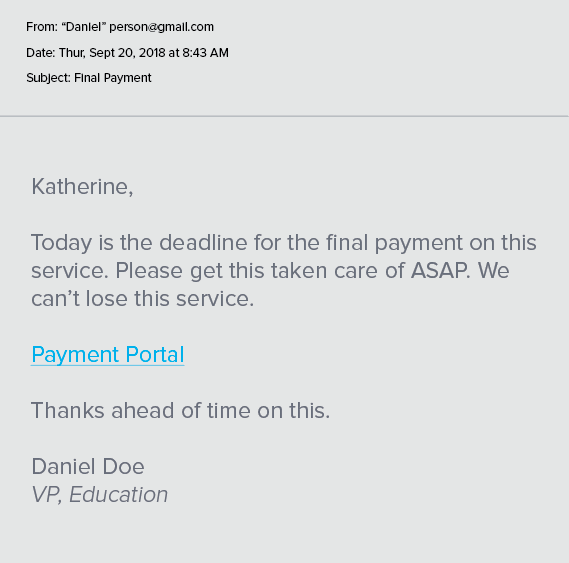
To make these scams more believable, multiple touchpoints will now be used: The fake account calling with questions and asking about specific details of the email (to make it more believable), additional emails from the requestor asking if they have talked to the accountants, and possibly supporting documents seemingly verifying this type of activity. Those documents could also include malware to gain direct access to the victim’s computer.
Remember: All these tactics will focus on urgency and secrecy. The number of touch points and contact is only added in to build on the fact this is urgent, and to confuse or fluster the target into completing the transfers.
What can I do to prevent being tricked by a BEC?
Start by recognizing the tactics used in a BEC. If you can see through the scam, you are already ahead of the game. Consider adding internal roadblocks to deal with BEC type situations.
- Follow up with the requester by calling or texting them; do not wait for them to contact you again, or reply to the same message. Try a different method of communication to contact the “requestor,” so if you get a hold of them and they’re as confused as you are, you know the request isn’t legit.
- Confirm the source of the communication. Is it the proper corporate email, proper phone number, the usual accountant or firm?
- Insert stringent steps and paperwork into the process. For instance, The need for two signatures on approvals, add multiple layers of approvals based on the dollar value of the request, or add a requirement that all paperwork for transfers be delivered before the transaction. And yes, even requests from the CEO should be subject to this process. Get their buy-in and support. It might just save them in the end.
- Consider what your senior executives post about travel on their social media profiles. Mentioning travel publicly provides an opportunity for fraudsters to impersonate them while they are potentially hard to reach.
Setting policies and enforcing them at all levels limiting the ability for one person to make or authorize a transfer of a large sum of money can help prevent scams and reduce your risk. Educating finance staff and having a plan in place for all transfers from your organization, starting at the top down, can help identify and stop these attacks.
Ultimately, build in safeguards to protect against Human 1.0, a software not easily patched and hard-wired to be helpful and empathetic towards others. Your business may depend on it.
This was originally posted on 250ok’s blog in 2018, updated here with 2019 numbers. March is Fraud Prevention month, be sure to protect yourself, your clients and your company.


