Featured Articles:
Latest News:
Email Deliverability Fundamentals: SPF
by Matt V - @emailkarma | Jan 15, 2026 | 2025 | 0
Email did not always include guardrails. In the early 2000s, inbox providers needed a practical...
Read MoreChecklist for Staying Out of Trouble
by Matt V - @emailkarma | Nov 19, 2025 | 2025 | 0
This is a little teaser for an upcoming Podcast episode. Chris and I covered far more than this...
Read MoreImage Caching and the Vanishing Accuracy of Open Rates
by Matt V - @emailkarma | Nov 11, 2025 | 2025 | 0
Open rates used to be a dependable measure of engagement. You could tell who opened, when, and...
Read MoreGmail Updates Sender Requirements and Bounce Codes
by Matt V - @emailkarma | Nov 4, 2025 | 2025 | 0
Gmail is tightening the screws on unauthenticated and non-compliant email starting November 2025.
Read MoreYahoo Sender Hub Introduces New Tools
by Matt V - @emailkarma | Oct 22, 2025 | 2025 | 2
Yahoo has launched Sender Hub Insights, a new dashboard offering marketers a closer look at how...
Read MoreGoogle Postmaster Tools v1 Retires
by Matt V - @emailkarma | Sep 25, 2025 | 2025 | 0
Google announced that they are officially closing the door on the old Google Postmaster Tools...
Read MoreLaposte Tightens Email Authentication Rules
by Matt V - @emailkarma | Sep 4, 2025 | 2025 | 0
Laposte.net is raising the bar for email authentication. Starting Tuesday, September 9th at 9am...
Read MoreMail Routing Changes Announced for AT&T
by Matt V - @emailkarma | Jun 24, 2025 | 2025 | 0
Big news in the world of email deliverability! Yahoo announced a significant change to the routing...
Read MoreUnderstanding DKIM FBL (Feedback) Configuration
by Matt V - @emailkarma | Jun 16, 2025 | 2025 | 0
Email is a crucial component of any brand’s communication strategy. Knowing how your emails...
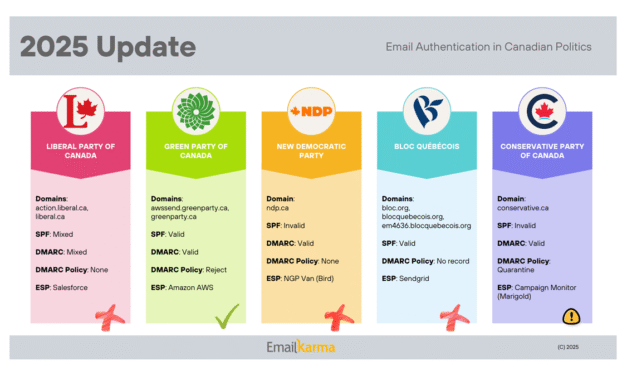
Read More2025 Email Authentication in Canadian Politics
by Matt V - @emailkarma | Apr 15, 2025 | 2025 | 0
Email authentication is a critical component of digital security, especially for political parties. The overall landscape in Canada is concerning.
Read MoreOutlook's 2025 Email Rules for Marketers
by Matt V - @emailkarma | Apr 2, 2025 | 2025 | 0
Microsoft Outlook tightens email authentication rules for high-volume senders to combat spam and phishing, starting May 2025.
Read MoreDMARC Alignment: Strict vs. Relaxed
by Matt V - @emailkarma | Mar 13, 2025 | 2025 | 0
Master DMARC alignment with strict vs. relaxed modes for SPF/DKIM. Enhance email security and deliverability effectively.
Read MoreSearch EmailKarma
Support these EmailGeeks!
| Deliverability Inferno: Helping Email Marketers Understand the Journey from Purgatory to Paradise – Chris Arrendale |
| Email Marketing Rules: Checklists, Frameworks, and 150 Best Practices for Business Success – Chad White |
| Holistic Email Marketing: A practical philosophy to revolutionize your business and delight your customers – Kath Pay |